We noticed that the JRE/JDK 8u351 update leads to a MicroEJ SDK license check failure ([M65] - License check failed [tampered (3)]).
The verification of JAR files signed with SHA-1 algorithm fails since JDK version 8u351 (see section “Disabled SHA-1 Signed JARs” of Java™ SE Development Kit 8, Update 351 Release Notes).
A fix for this issue is provided in MicroEJ Architectures since version 7.18.1.
If you cannot update your Architecture version, several workarounds can be applied. Those workarounds consists in allowing JARs signed with SHA-1 algorithm by modifying the JDK Security Property jdk.jar.disabledAlgorithms.
Workaround 1 - Define your Own Security Property
-
Download and unzip the following security property file: microej.jdk.security.zip (233 Bytes),
-
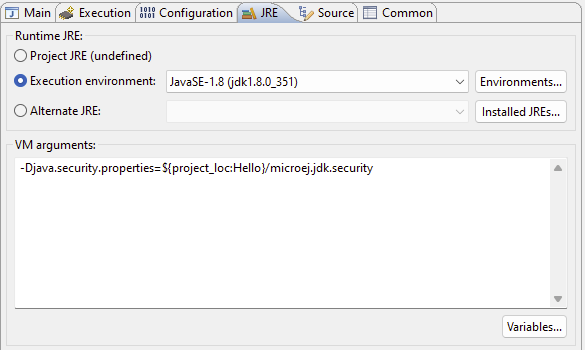
When building your application from a MicroEJ SDK launcher, the security property file’s path needs to be specified in your MicroEJ application launcher:
- Add the following property to the
VM argumentssection of theJREtab of your launcher:
-Djava.security.properties=<path_to>/microej.jdk.security
- Add the following property to the
-
When building your application with
Build Module:- Add the following property to the
module.ivy:
<ea:property name="launch.properties.jvm" value="-Djava.security.properties=<path_to>/microej.jdk.security"/> - Note that the property can also be added in a settings file provided to MMM, see MMM Options documentation:
launch.properties.jvm="-Djava.security.properties=<path_to>/microej.jdk.security"
On Windows, use double backslashes\\as path separator.
- Add the following property to the
-
When building your application with MMM Build Kit, the security property file’s path needs to be specified when calling the
mmmCLI:- Add the following property to the command line:
-Dlaunch.properties.jvm="-Djava.security.properties=<path_to>\microej.jdk.security"
- Add the following property to the command line:
Workaround 2 - Edit the Security File of the JDK or JRE
You can also edit the Security file of your JDK or JRE installation to apply this workaround to your entire environment:
- Edit the file
<jdk_home>/jre/lib/security/java.securityor<jre_home>/lib/security/java.security - Modify the definition of the property
jdk.jar.disabledAlgorithmsto remove the parametersSHA1 denyAfter 2019-01-01:jdk.jar.disabledAlgorithms=MD2, MD5, RSA keySize < 1024, \ DSA keySize < 1024, include jdk.disabled.namedCurves
Alex for MicroEJ