Porting MicroEJ virtualized container to embedded Linux unlocks a flexible, scalable foundation for modern device software. Unlike bare-metal deployments or integration with RTOSes such as FreeRTOS or Zephyr, Linux provides a robust user-space environment and a wealth of system level services, making it an ideal host for running the MicroEJ Virtual Execution Environment (VEE) alongside other applications.
This article guides developers through the essential integration principles and architectural concepts when porting MICROEJ VEE to Linux.
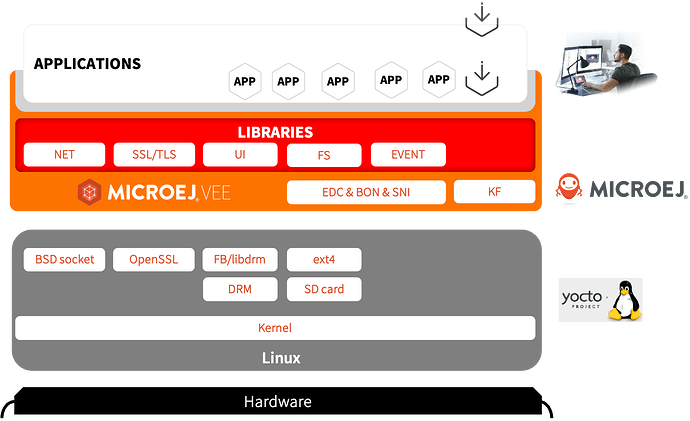
Example of implementation of Linux MicroEJ VEE
Linux or MCU/RTOS platforms? For MicroEJ VEE Ports, it makes no signicative differences, enjoy the same level of consistency and efficiency across different systems. MicroEJ VEE Ports containerization also enables the reuse of existing applications, significantly reducing development time and costs. Developers can leverage the streamlined ecosystem of a Linux platform through MicroEJ VEE as easily as MicroEJ VEE can be tuned to adapt to lower cost MCUs and resource availability.
User-Space Execution Architecture
On top of Standard Linux and POSIX APIs
At its core, MICROEJ VEE runs entirely in user space as a single standard Linux process. As such, there is no need for kernel modules, privileged components, a specific kernel version, or any particular third party C library for the core runtime.
VEE’s integration is handled through a lightweight C-based Abstraction Layer that maps the core engine and libraries’s low-level APIs to Linux own APIs. As long as the target environment provides standard POSIX compatibility, you should have no problem integrating MicroEJ VEE port reliably with standard C libraries such as glibc, musl, or uClibc. Moreover the Abstraction Layer taps into native Linux facilities, threads, file and network I/O, device-specific interfaces, timers, ensuring both portability and straightforward maintainability.
Specialized Libraries and Package Updates
Certain optional libraries used in MICROEJ VEE may rely on external components. For instance, secure sockets or cryptographic features may depend on OpenSSL (or an equivalent crypto backend), while graphical capabilities may require access to the Direct Rendering Manager (DRM). Integration of these components remains flexible and can be adapted to the target system configuration.
Speaking of system configuration, integrators are free to choose the update manager best suited to their environment. As long as libraries are compatible, VEE will continue to run, the stickyness to the underlying kernel or library versions is low. This loose coupling architecture avoids the complexity and risk associated with kernel modifications, and it easily adapts to different Linux distributions as long as common APIs are available.
Service Management and Init Integration
Due to being a single process, you can launch MICROEJ VEE instances just as any other application via systemd service units, custom init scripts, or interactively. MICROEJ VEE does not force you into any specific init system.
Internally, the VEE runs its own service framework, governing the lifecycle and dependencies of applications within the virtual environment itself. This separation keeps the VEE’s orchestration logic independent of the wider OS, simplifying integration and ensuring predictable behavior across deployments.
Memory Usage and Host Requirements
There are no RAM or memory cap constraints imposed by the VEE on the system. Its memory footprint is limited to the address space provided by the host OS, which can be tuned per deployment. VEE also does not offload its memory consumption to external services, and it lowly impacts existing processes.
Build, Bootloading and Trust
Build System Integration
MICROEJ VEE is distributed as an ELF executable along with its native libraries. It can be built, installed, and managed like any standard Linux application. The build system is compatible with any Linux toolchain (Yocto and otherwise, cross-compilation or not). This flexibility enables consistent packaging for custom Linux images and integration across diverse hardware and product variants.
Secure Boot and TEEs
MICROEJ VEE is fully compatible with Secure Boot and Trusted Execution Environments (TEEs) such as OP-TEE on ARM systems. While it does not integrate directly with boot or TEE mechanisms, the VEE can run as a signed binary in a secured platform environment. Within the VEE, application authenticity and integrity checks can be enforced at the package level, with the VEE verifying digital signatures before execution.
Security
Linux Security and MicroEJ Security
Out-of-the-box, the VEE does not require privileged execution or specialized LSM (Linux Security Module) policies (SELinux or AppArmor) nor does it provide predefined LSM profiles. Instead, application-level isolation is handled via the VEE’s own sandbox model using the Java Security Manager which intercepts and governs all application-level access to filesystems, devices, and network functions through configurable policies.
More information on the security policy model is available in the MicroEJ documentation at Define a Security Policy — MicroEJ Documentation .
Application Isolation and Resource Control
Beyond security policies, VEE enforces stringent resource boundaries between applications. Each application runs in an isolated memory space, with CPU utilization and system resource access governed by an internal Resource Manager and a preemptive, priority-aware scheduler. Filesystem and network activity is mediated by VEE APIs and configurable permissions, further isolating apps from each other and from a direct access to POSIX APIs. This ensures that resource-starved or faulty applications cannot corrupt both MicroEJ applications and Linux processes.
Crypto
OpenSSL is a widely used open-source library that provides the essential cryptographic algorithms and features needed to enable secure communications on Linux and embedded systems. In the context of MICROEJ VEE, OpenSSL serves as one of the supported native crypto engines for the Security Foundation Library.
Using OpenSSL as a back-end enables strong encryption, certificate management, digital signatures, and secure random number generation. This approach allows applications to use secure transmissions, essential for any connected system in the IoT space. The VEE abstracts OpenSSL via dedicated low-level C APIs (LLSEC_*.h) and exposes them through the Security library for managed code (a standardized Java APIs that comply with the Java Cryptography Architecture), providing convenient and reliable access to industry-standard cryptography and SSL/TLS protocols.
Summary
In summary, porting MICROEJ VEE to Linux is efficient, non-intrusive, and leverages the industry’s best practices for embedded software packaging, security, and update management. Its clean separation from the kernel and use of standard deployment conventions mean it fits comfortably into both enterprise and bespoke embedded environments making it an ideal choice for modern IoT and smart devices.
Going further
- Try MicroEJ SDK6 getting started for NXP i.MX93 Freedom board on i.MX 93 FRDM & EVK Boards — MicroEJ Documentation
- Check Generic Abstraction Layer for Linux VEE Ports on GitHub - MicroEJ/AbstractionLayer-Linux: MicroEJ Abstraction Layer implementation for Linux.
- Demos:
- Video Real-Time Multi-Device Sync on NXP i.MX93 & RW612 https://www.youtube.com/watch?v=1fx8rNlyX_A
- Video Dynamic app deployment https://www.youtube.com/watch?v=UXYZDulPsoc